UPDATED: Hack Track: #Twitterhack bitcoin scam

Merkle Science

This article has been updated as of 27 July 2020 — our latest analysis is included at the end of this post.
On Wednesday, 15th July 2020 the global social media platform Twitter suffered a major security breach whereby hackers hijacked the verified accounts (those with blue checkmarks) of major politicians, business leaders, celebrities, and companies with millions of followers and promoted a bitcoin investment scam.
Some of the compromised accounts belonged to Joe Biden, Barack Obama, Elon Musk, Bill Gates, Apple and several cryptocurrency firms including Binance and Gemini. The bitcoin scam asked followers of the compromised Twitter accounts to send bitcoin to a specific wallet address with the promise that double the amount of funds would be sent in return. Many of the scam Tweets contained the following content:
“Due to Covid-19, we are giving back over $10,000,000 in Bitcoin!
All payments sent to our address below will be sent back doubled.
BTC address: bc1qxy2kgdygjrsqtzq2n0yrf2493p83kkfjhx0wlh
This is only going on for the next 30 minutes! Enjoy!”
The hack took place over the course of several hours on Wednesday and Twitter responded by preventing verified accounts from tweeting and locking the compromised accounts while the company continued to investigate the incident. In several tweets by Twitter Support on Wednesday evening the company attributed the account hijacking to a “coordinated social engineering attack” on its employees which provided an opportunity for the hackers to access “internal systems and tools”.
There is widespread speculation about the root cause of this hack including that this was in fact an “inside job” and some news reports cite “evidence” of hackers claiming to have bribed Twitter employees to help orchestrate this event. Whatever the reasons behind the incident, the fact that this occurred across so many accounts on one of the world’s largest social networks is troubling and it does not help with bitcoin’s reputation, already soured by earlier associations with criminality and the darknet.
Our Initial Analysis of the Incident
However, thanks to the transparency of the bitcoin blockchain, Merkle Science’s Data Intelligence team has been tracing the funds sent to and from the bitcoin addresses provided in the scam tweets and so far we have found that more than US$120,000 equivalent in bitcoin has been scammed off cryptocurrency holders across the globe. Below is a summary of our analysis.
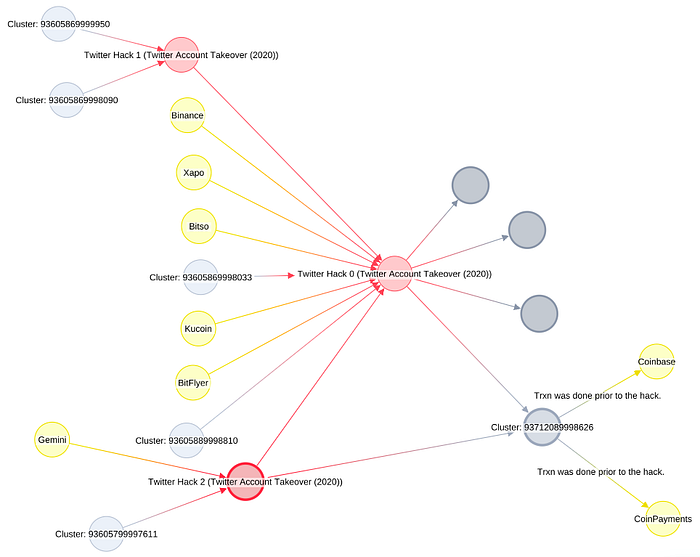
As seen in the screenshots above, the bitcoin address bc1qxy2kgdygjrsqtzq2n0yrf2493p83kkfjhx0wlh, which we have code-named Twitter Hack 0 is cited in several of the scam tweets from the compromised accounts. As of Thursday, 16th July 23:00 SGT this address has received BTC 12.86 or roughly US$120,000 equivalent from 323 incoming transactions, most likely from individuals falling victim to this scam.
Incoming Transaction Analysis
Through blockchain transaction analysis, Merkle Science’s team was able to derive more insights into the fund flows for the Twitter Hack 0 address:
- The address bc1q0kznuxzk6d82e27p7gplwl68zkv40swyy4d24x, code-named Twitter Hack 1, has received a total of BTC 0.17828423 or US$ 1,625 equivalent from 14 incoming transactions and all the funds have been sent to the main scam address Twitter Hack 0.
- Address bc1qwr30ddc04zqp878c0evdrqfx564mmf0dy2w39l, that we referred to as Twitter Hack 2, has received BTC 0.55302586 or US$ 5,038.39 from 36 incoming transactions. Of these, 0.63% of the funds are coming from a user account belonging to the exchange ‘Gemini’.
- 50.13% of the funds in the Twitter Hack 2 address have been sent to the Twitter Hack 0 address.
- The Twitter Hack 0 address has received a total of BTC 12.86584703 from 323 transactions, of which 5.2% are incoming funds from user accounts at Binance, Bitflyer, Xapo, Kukoin, and Bitso exchanges.
Outgoing Transaction Analysis
45% (BTC 5.817) of the funds from the Twitter Hack 0 address have been transferred to an unidentified “cluster”, or group of connected addresses, labeled in our platform as 93712089998626 and 6.45% (BTC 0.83) of the funds have been transferred to three different addresses:
- bc1qas2rvpejpvncd6z5hcscvw52n4wxw5th2de67v
- bc1qs0tglr6gfc90q7ngw4yynvl2cmyvlhdqehwy4f
- bc1q7jy39ducamer90t4a68y6jhzakvdqlps4ynhs5
The funds from these three addresses have not moved yet.
The remaining 47.66% (BTC 6.16) of the funds remaining in the address Twitter Hack 0 have also not yet been moved.
The 93712089998626 clusters is comprised of 13 addresses which in turn are sending funds to multiple addresses. Recipient addresses in this cluster have also sent bitcoin to addresses associated with Coinbase and Coinpayments prior to the scam taking place.
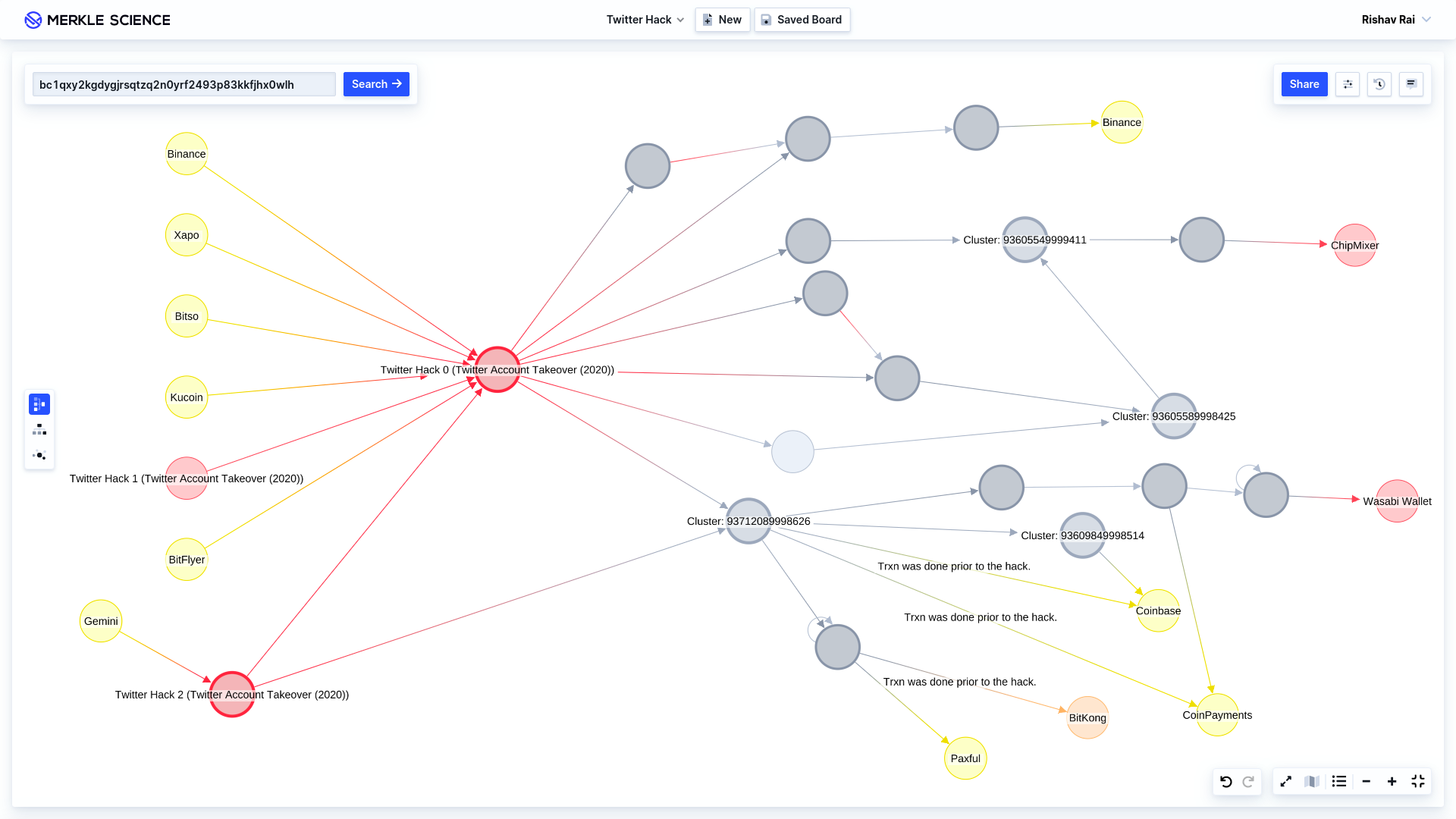
UPDATED Analysis — as of Monday, 20 July 2020
The cluster of bitcoin addresses linked to Twitter Hack 0 (see above) contains 10 different addresses (including the main hack address), which means all these addresses are controlled/owned by the hacker. More than 99.99% of the funds from this cluster have been transferred to other addresses.
Based on our analysis* it seems the hackers have transferred the bitcoin to addresses associated with several exchanges including Binance, Paxful, and CoinPayments. The breakdown is as follows:
- BTC 0.0011 transferred to Binance
- BTC 0.016 transferred to Paxful
- BTC 0.0090 transferred to CoinPayments
The hackers have also used coin mixing services such as Wasabi Wallet and ChipMixer to obfuscate the flow of funds:
- BTC 2.89 transferred to Wasabi Wallet
- BTC 0.1092 transferred to ChipMixer
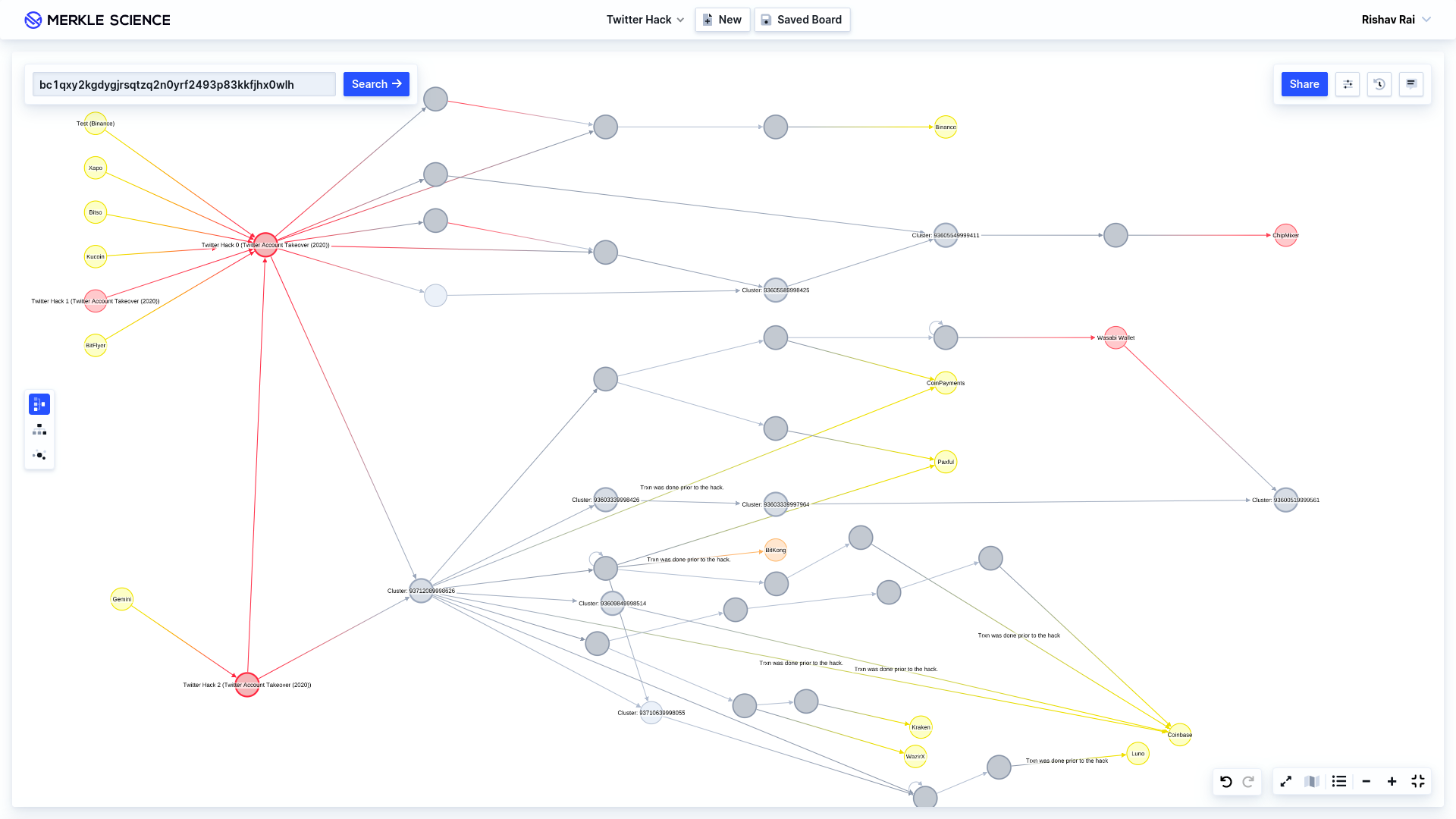
LATEST Analysis — as of Monday, 27 July 2020
The hackers have transferred more bitcoin from the known associated address clusters (see above) to addresses associated with exchanges Kraken, Wazirx, Coinbase, and Paxful, the breakdown is as follows:
- BTC 0.086 transferred to Kraken
- BTC 0.1 transferred to Wazirx
- BTC 0.15 transferred to Coinbase
- BTC 0.106 transferred to Paxful
Merkle Science’s data intelligence team will continue to monitor the bitcoin addresses associated with the Twitter Hack scam and we will update this article should further fund movements occur. These addresses have already been labeled in our blockchain transaction monitoring and blockchain forensics tools.
*Merkle Science uses proprietary heuristics algorithms to determine cryptocurrency address clusters and the entities labeled in our database are manually verified by our data intelligence team.
In the past, we have come across multiple bitcoin-themed celebrity impersonation scams that have taken place across various platforms including YouTube, Twitter, Reddit, and Bitcointalk. This is the first time so many prominent Twitter accounts have actually been hijacked simultaneously rather than spoofed so we will be curious to see how the nature of cryptocurrency scams evolve in the months ahead and of course how Twitter and other social media platforms respond to such threats.
If you would like further information about Merkle Science’s blockchain transaction monitoring and forensics tools and our intelligence reporting services please email contact@merklescience.com.
About Merkle Science
Merkle Science provides blockchain transaction monitoring and intelligence solutions for cryptoasset service providers, financial institutions and government agencies to detect, investigate and prevent the use of cryptocurrency for money laundering, terrorist financing, and other criminal activities. Merkle Science is headquartered in Singapore with offices in Bangalore, Seoul, and Tokyo and backed by Digital Currency Group, Kenetic, SGInnovate and LuneX.


