Hack Track: Mixin Flow of Funds Analysis

Merkle Science

Mixin Network, a Hong Kong-based digital asset transactional platform, reported a security breach on 25 September, revealing a loss of approximately $200 million due to a hack of its cloud service provider. The stolen funds accounted for so far are comprised of ETH, USDT (swapped to DAI), and BTC. If the $200M figure stated by Mixin is accurate, it would make this incident the biggest hack of 2023 so far.
This unfortunate event marks the second significant cryptocurrency breach in Hong Kong this month, underscoring the persistent challenges faced in safeguarding digital assets, despite regulatory efforts.
What is Mixin Network?
With the mission to put convenience, security, and privacy in digital assets and messages first, Mixin Network claims to be a free, lightning-fast peer-to-peer network for digital assets.
Response to the Incident
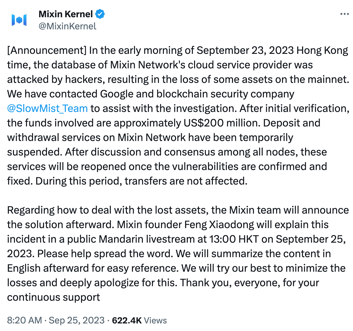
In response to the incident, Mixin Network announced on Twitter, "In the early morning of September 23, 2023, Hong Kong time, the database of Mixin Network's cloud service provider was attacked by hackers, resulting in the loss of some assets on the mainnet."
Mixin Network announced the hack on Twitter
Founder Feng Xiaodong expressed their commitment to minimizing the impact on users' assets stating:
“No matter what your assets are — whether it's Bitcoin or Ethereum — we will ensure that half of it is unaffected. We’re trying to find a way to recover the compromised money, but that is very difficult.”
Mixin Network has extended an offer of a $20-million bug bounty in exchange for the safe return of the remaining funds.
This message was encrypted within a transaction, appealing to the perpetrator to return the ill-gotten gains, since the majority of the stolen funds belong to innocent users.
Merkle Science’s Flow of Funds Analysis
Merkle Science's Blockchain Forensics Tool 'Tracker' visualizing the flow of funds
Merkle Science's investigations reveal that the attackers drained over 11,400 ETH wallets and 127 Bitcoin wallets during the breach, resulting in a total loss exceeding $144 million in Bitcoin, Ethereum, and USDT tokens.
The address Exploiter 1, through a series of more than 10,000 transactions, received a total of 59,807 ETH from more than 11,400 Mixin wallets, which is equivalent to approximately $94 million.
The address Exploiter 2 received more than 23.5 million USDT from Mixin which was then sent to a swap protocol and converted into approximately 23.5 million DAI.
A similar trend was noted when 891 BTC were transferred from 127 Mixin wallets to the Exploiter’s address via 3 transactions.
At the time of investigation, the funds were currently unmoved and the exploiter’s addresses currently held the stolen $144 million.
Attackers pilfered this amount in the following tokens:
|
Token Symbol |
Token Amount |
USD Value |
|
USDT |
23,569,774.0801 |
23,565,287.43 |
|
ETH |
59,808.0106 |
96,464,159.33 |
|
BTC |
891 |
24,101,419.61 |
|
Total |
144,130,866.37 |
(Note: The above analysis is the result of an ongoing investigation, with almost $50 million worth of assets still to be accounted for)
Emerging Trends in Money Laundering Techniques
The advent of evolving technologies such as decentralized protocols and cross-chain bridges has significantly diminished barriers hindering the unrestricted flow of funds across diverse blockchains. Swaps operate within a decentralized framework, thereby obviating the need for individuals to log in or create accounts.
Furthermore, swaps are employed to obfuscate the traceability of funds. When swaps are utilized, it becomes notably challenging to discern the exit points of funds within the blockchain. In contrast, in the case of exchanges, blockchain analytics firms can assist law enforcement agencies (LEAs) in identifying the addresses responsible for laundering funds acquired from hacks, along with the precise amounts and transaction details. This is feasible due to the account and KYC (Know Your Customer) requirements imposed by exchanges. Conversely, swaps and bridges operate without necessitating user accounts or KYC information, rendering them immune to such scrutiny.
Merkle Science has taken immediate action to ensure that wallets associated with the Mixin hack have been tagged across all our tools. This shows direct/indirect exposure to wallets involved in the theft.
Moreover, our forensics tool 'Tracker' has been optimized for investigating DeFi and smart contract transactions with a watchlist feature that notifies users about any incoming/outgoing movement in funds from the attacker's address.


