Hack Track: ETERBASE Cryptocurrency Exchange

Merkle Science

Merkle Science Hack Track provides digestible insights on the movement of stolen funds from the latest cryptocurrency heists.
[Scroll below to skip to our analysis of the stolen fund movements]
Who was hacked?
Based in Slovakia, ETERBASE is a European cryptocurrency exchange.
What was stolen?
Announcing the hack on Twitter on Tuesday (Sept. 8), ETERBASE said that six of its cryptocurrency wallets, containing bitcoin (BTC), ether (ETH)/ ERC-20 tokens, XRP, Tron (TRX), Tezos (XTZ), and Algorand (ALGO), have been compromised.
How much was stolen?
According to research by The Block, more than US$ 5 million equivalent in cryptocurrency funds has been stolen.
When did the hack take place?.
According to ETERBASE’s statement, the hack took place on the night of Monday (Sept. 7). However, it is likely the hackers would have gained access to ETERBASE servers several hours or possibly even days prior to the funds being stolen to retrieve the private keys used to sign the outgoing transactions.
Why did the hack take place?
Similar to Upbit’s hack, this is another case where the stolen cryptocurrency stored in a hot wallet (where the private keys are available in a database connected to the internet) that did not require multiple signatures (multi-sig) by operators of the exchange to sign an outgoing transaction.
Therefore the hackers are able to retrieve the wallet’s private keys and sign the subsequent outgoing transactions without significant challenges. The full details regarding the cause of the hack have not yet been disclosed by ETERBASE.
How do we know this hack happened?
ETERBASE confirmed through an official statement on Tuesday (Sept 8) that its hot wallets were compromised on Monday night.
What is the impact of the hack on the firm’s clients?
In the statement on Telegram, ETERBASE assured its clients that the exchange is taking all necessary steps to ensure that their deposits don’t suffer any attack as a result of the attack. Also, the exchange is under maintenance and currently not accepting deposits and withdrawals.
How does this hack compare to others?
ETERBASE is the second European cryptocurrency exchange to suffer a cyber-heist in 2020, after Altsbit, which in February this year, lost almost all its funds.
Where are the stolen funds going?
Announcing the hack on Tuesday, ETERBASE said that six of its addresses, tied to bitcoin (BTC), ether (ETH)/ ERC-20 tokens, XRP, Tron (TRX), Tezos (XTZ), and Algorand (ALGO), have been compromised. In this article, let’s examine two high-value cryptocurrencies, i.e., bitcoin and ether, from this hack.
Bitcoin fund movement analysis:
- Initially, 11.45 stolen BTC were transferred from Eterbase Hot Wallet Address (17qQhHmNs9X3D4YWqvkp6St1YSsXWPdAty) to the hackers’ main address (1ANLZZ2YFGumRXaD3EMii92zWQgvX2CK9c) on 8th September 2020.
- The hackers’ main Address is part of a cluster, let’s call it: ‘Cluster A’, which has 14 bitcoin addresses.
- ‘Cluster A’ was first and last active on 8th September 2020, during the hack. The cluster has received a total of 192.27 BTC. ( Eterbase=11.45 BTC, 99.01 from two cryptocurrency exchanges, one of which is a well-known major exchange, and remaining from unidentified addresses/clusters).
- One crucial point to note is that the transfer of funds from two different cryptocurrency exchanges happened after the Hack. The Hackers already had funds in their existing accounts on these exchanges and after the hack, they consolidated all their funds together into ‘Cluster A,’ to evade account seizure by these exchanges.
- All the funds from ‘Cluster A’ were transferred to BTC address 15b38XQPXV68huxMUwUcwEQm7hUdzLwQiD (let’s call it ‘Address A’) in one single transaction in an attempt to consolidate all funds (hacked+genuine funds) to this address. The ‘Address A’ also received more than 165 BTC from a well-known Exchange based in Hong Kong, after the hack.
- ‘Address A’ received more than 469 BTC at the time we concluded this research.
- The hacker transferred 430.39 BTC out of 469 BTC to two different addresses 330.39 BTC to 1GeFr6ZRV6o3SRhkNLvTvJep9LixkC1MvW and 100 BTC to 3NcUCyUHbjes3Yds93JnU6dxKtPpei4i5Z. The final balance of the ‘Address A’ is 38.70 BTC and the address is still active.
- Funds from the last two bitcoin addresses have been transferred to one-time use addresses using a common method of Chain Peeling. The hackers here are attempting to divide the larger funds into smaller funds before sending it to various exchanges for liquidating.
- Hackers also received 0.02 BTC from an exchange-based in the US and 0.15 BTC from a gaming entity, most likely their own funds.
- At the time of the conclusion of this research, hackers had sent more than 8.5 BTC to one of the largest cryptocurrency exchanges in the world for liquidation.
Ethereum fund movement analysis:
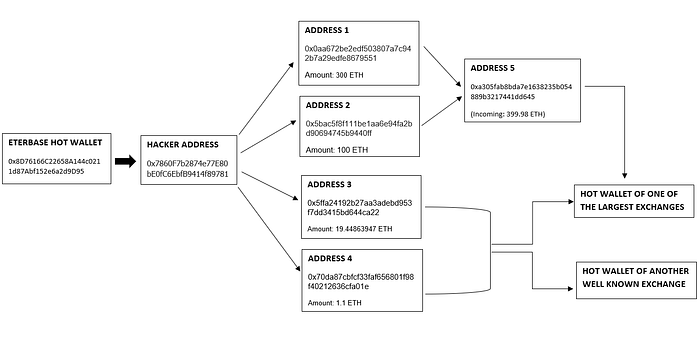
- On 8th of September 2020, 387.4028 ETH were transferred from the Eterbase hot wallet address (0x8D76166C22658A144c0211d87Abf152e6a2d9D95) to the hackers’ main address (0x7860F7b2874e77E80bE0fC6EbfB9414f89781aD9) through the transaction id : 0x5e86a4f450817e30d212bf12bdd20da2f77198f7519fae90fb6a840ea1057a5e
- The hackers’ main address (0x7860F7b2874e77E80bE0fC6EbfB9414f89781aD9) received an additional sum of 0.66 ETH from 2 unidentified addresses through a series of 5 transactions, after the hack.
- The Hacker’s main address was active for a total of 10 hours on the September 8th and there were multiple smart contract transactions during this time and 7 outgoing transactions to 4 different ETH addresses, the details of which are as follows:
- 95% of the stolen Ether has been transferred from the addresses 0x0aa672be2edf503807a7c942b7a29edfe8679551 and 0x5bac5f8f111be1aa6e94fa2bd90694745b9440ff to another address 0xa305fab8bda7e1638235b054889b3217441dd645, which is active for over 2 years. Apart from this, there have been small transactions from the other recipient addresses (0x5ffa24192b27aa3adebd953f7dd3415bd644ca22, 0x70da87cbfcf33faf656801f98f40212636cfa01e) to multiple addresses including but not limited to the hot wallets of some of the most prominent cryptocurrency exchanges.
- Off all the funds that the address 0xa305fab8bda7e1638235b054889b3217441dd645 has received since it first appeared on the blockchain, almost all the funds have been transferred to the hot wallet of one of the largest cryptocurrency exchanges among other smart contract transactions. This is a strong indication that the address 0xa305fab8bda7e1638235b054889b3217441dd645 is most likely controlled by the same exchange.
- The total funds stolen in ETH were approximately USD 146,000 and almost all of the stolen Ether finally ended up in the hot wallet of this major cryptocurrency exchange.
- The majority of the gain that the hackers have benefited from is the stolen ERC20 Tokens which might have been converted into Ether or swapped for other coins/tokens.
What do we know about the hackers so far?
- Hackers already had a lot of funds (>180 BTC) in different exchanges.
- After the hack, the hackers consolidated the funds and started to divide the funds into smaller amounts.
What can be done to prevent hackers from cashing out?
In its statement as published by Coingeek, ETERBASE said that the company has contacted all centralized exchanges that might be receiving the stolen funds.
All exchanges that are receiving funds from ETERBASE wallets can freeze the account of the user associated with the incoming transaction (flagged by a blockchain analysis tool), preventing them from trading one currency for other cryptocurrencies, especially anonymous ones, that could then be transferred elsewhere and are more difficult to trace.
Merkle Science has also updated wallet addresses associated with the Eterbase hack. All our partners and customers will also receive immediate information if any funds they receive are from the hackers’ wallet
Most exchanges globally share information on stolen fund addresses to deal with such risks and collaborate with law enforcement agencies and blockchain analysis firms such as Merkle Science for additional data and investigative services.
— -
Our team will continue to update this article on a periodic basis following continuing movements of the stolen funds


